Overview
IP Fabric supports discovery of network devices via dedicated Vendor APIs.
Currently, the following Vendor APIs are supported (as listed in Settings → Discovery & Snapshots → Discovery Settings → Vendors API → + Add → Type):
- AWS
- Azure
- Check Point Management
- Cisco APIC
- Cisco FMC
- F5OS
- Forcepoint
- Google Cloud Platform
- Juniper Mist
- Meraki REST
- Prisma
- Ruckus Virtual SmartZone
- Silver Peak
- VeloCloud
- Versa
- Viptela
- VMware NSX-T
These APIs are often complementary to the CLI-based discovery process for established networking vendors but are essential for SD-WAN or cloud vendors.
This section describes per-API specific settings for supported APIs.
For each Vendor API, additional system settings can be applied.
Multi-Factor Authentication
When configuring login credentials for Vendor API, please note that IP
Fabric does not support multi-factor authentication (MFA). Please use a user
account without MFA enabled (you may have the option to generate an
application access token).
Slug and Comment
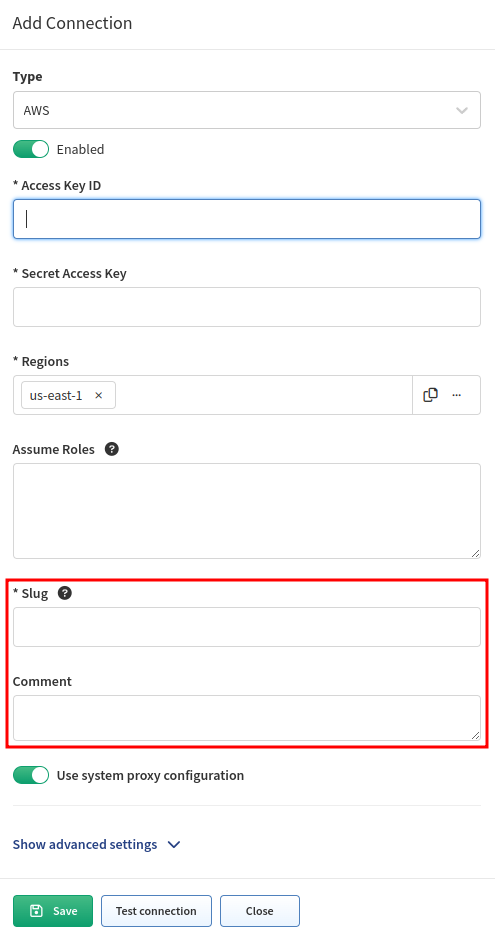
Every instance of Vendor API configuration has two additional fields (the example screenshot shows the AWS configuration).
- Slug
-
A slug must be unique and not empty. It is included in logs and other places to distinguish among potentially multiple API instances (think about it as the
loginIPfor the API). We recommend using short and descriptive values, such asaws-us,aws-jp, etc. -
Since version
6.3, aSlugcan only containa-zA-Z0-9_-. Previously created configurations will be automatically modified by removing not-allowed characters from theSlugaccording to the new validation rules. -
Slug?
Slug has many meanings, but in the computer world, it has become a term for the unique identifying part of a web address, typically at the end of the URL. For more information, see https://developer.mozilla.org/en-US/docs/Glossary/Slug.
- Comment
-
An optional free-text field for you to capture additional information about the API instance.
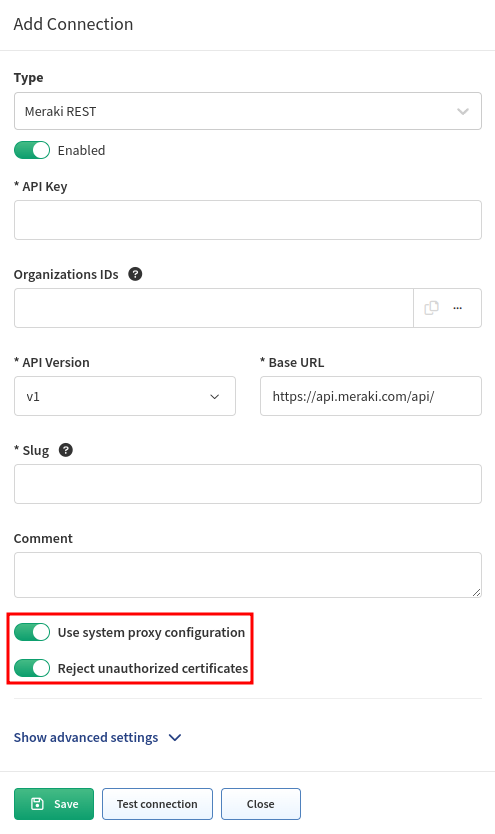
Use System Proxy Configuration
The system proxy is by default used for communication from IP Fabric to the Internet (e.g., for IP Fabric and system updates).
Some Vendor API controllers might be on the Internet or other parts of the network, and sending traffic through the system proxy might be required.
This setting can be enabled/disabled per Vendor API.
Reject Unauthorized Certificates
Due to security reasons, accepting unauthorized certificates might be undesired.
This setting can be enabled/disabled per Vendor API.
Advanced Settings
Since version 6.5, it has been possible to fine-tune the following advanced settings
for each Vendor API in the GUI (without going directly to the database):
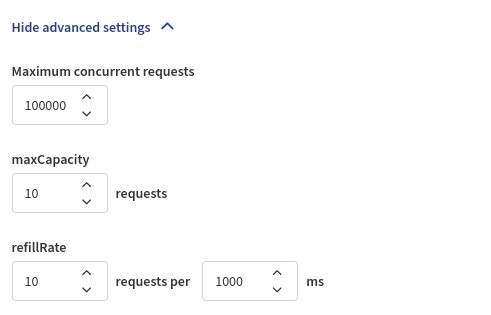
- Maximum concurrent requests
- Maximum amount of API calls to a device that can run in parallel.
maxCapacity(number of requests)refillRate(number of requests per specified milliseconds)
These are the default values for Meraki REST: