Azure Networking
Starting from version 4.3, IP Fabric supports discovery of the Azure Cloud
infrastructure. Azure devices are discovered only through API. IP
Fabric covers the IaaS (Infrastructure as a Service) part of the cloud.
Azure Cloud Compute provides an abstract view of the Azure physical
infrastructure.
- Virtual Network
- NAT Gateway
-
Virtual Network Gateway (both types: VPN and ExpressRoute) and devices related to a Virtual WAN solution:
- Virtual HUB
- VPN Gateway (the same functionality as VNGw type VPN)
- ExpressRoute Gateway (the same functionality as VNGw type ExpressRoute)
Since version 7.2, IP Fabric has introduced support for Load Balancers and Application Gateways.
Azure Setup
To add Azure devices to the global discovery settings, go to Settings →
Discovery & Snapshots → Discovery Settings → Vendors API, click + Add,
and select Azure from the list.
IP Fabric requires the following to connect to the Azure API:
- Tenant ID
- Client ID (application ID)
- Client Secret (application secret)
Since version 6.7, the Subscription IDs field is optional. Leave it empty to discover all available subscriptions within the same tenant.
Follow these steps to get the required data.
First, log in to the Azure portal.
Register an App
Search for Active Directory.
- From the left menu, click App registrations, then click +New registration.
- Fill in the name of the application (e.g.,
IP Fabric). From the Supported account types, select the first option, Single Tenant. Leave the other options blank. - Once you click Register, you’ll be redirected to the App overview page. Note the Application (client) ID and Directory (tenant) ID.
- Click Certificates & Secrets and select the Client secrets (0) tab, click + New secret, select Expiration, and then click Add.
- Copy the created client secret to the clipboard (column Value). You won’t be able to see it again.
Subscription & Access Control
Search for Subscriptions and select the subscription you like to add to IP Fabric (IP Fabric can do discovery per subscription).
- On the overview page, note the Subscription ID.
-
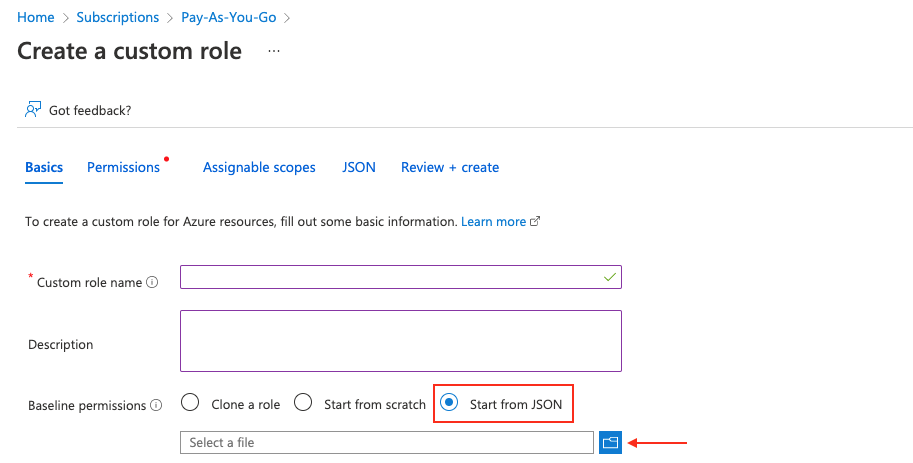
From the left menu, click Access control (IAM), click + Add, and then Add custom role. Fill in the role name. IP Fabric requires specific permissions to make API calls. Select Start from JSON and upload the JSON file with the required permissions (find it at the very bottom of this page). Click the Next button to continue.
-
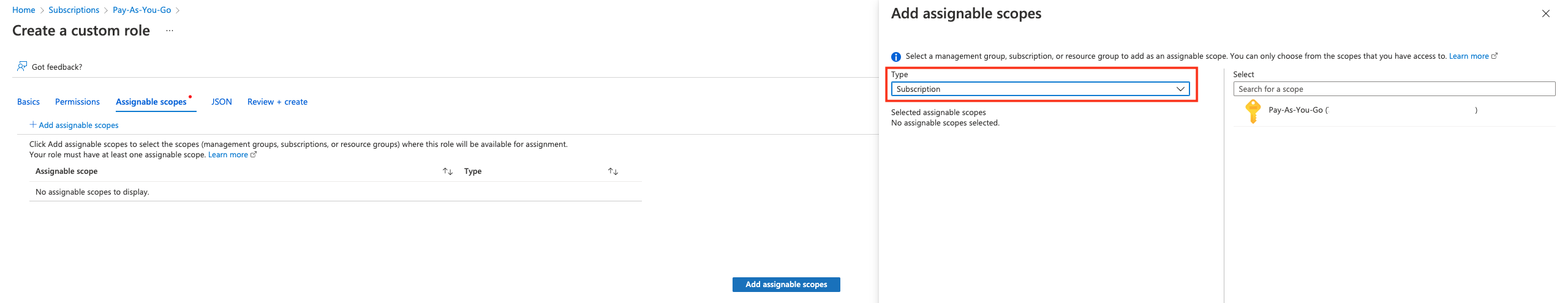
Review the permissions and click Next. Now you must assign a scope for this role. Click Add assignable scopes and from the right panel, select Type: Subscription, and then click the Subscription you want to assign.
-
Click Review + Create.
- Now you must assign the newly created Role to the Registered App. From the left menu, select Access control (IAM) again, then click + New and Add role assignment.
-
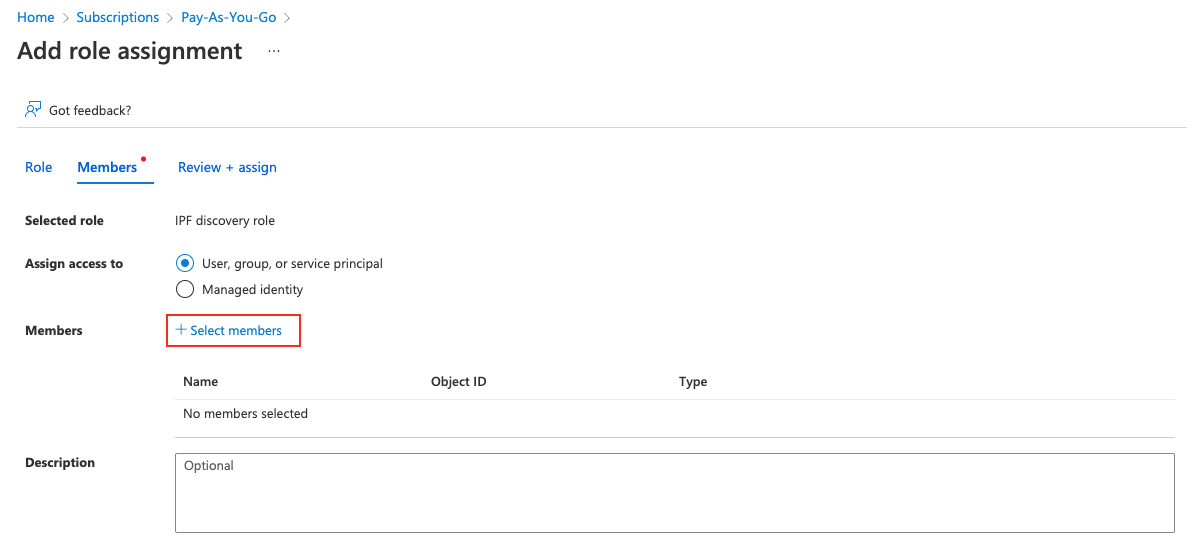
Find the previously created role, click Next, and then click + Select members. Find the app you created before. Click Review + Assign.
Role Definitions for IP Fabric
The following JSON format applies to IP Fabric version 7.5 and above:
{
"properties": {
"roleName": "IPF discovery role 7.5",
"description": "Permissions needed for IP Fabric to discover Azure network infrastructure",
"assignableScopes": [],
"permissions": [
{
"actions": [
"Microsoft.Compute/galleries/images/read",
"Microsoft.Compute/virtualMachines/instanceView/read",
"Microsoft.Compute/virtualMachines/read",
"Microsoft.Compute/virtualMachines/vmSizes/read",
"Microsoft.Network/*/read",
"Microsoft.Network/connections/getikesas/action",
"Microsoft.Network/networkInterfaces/effectiveNetworkSecurityGroups/action",
"Microsoft.Network/networkInterfaces/effectiveRouteTable/action",
"Microsoft.Network/virtualHubs/effectiveRoutes/action",
"Microsoft.Network/virtualNetworkGateways/getbgppeerstatus/action",
"Microsoft.Network/virtualNetworkGateways/getlearnedroutes/action",
"Microsoft.Network/vpnGateways/vpnConnections/vpnLinkConnections/getikesas/action",
"Microsoft.Resources/subscriptions/locations/read",
"Microsoft.Resources/subscriptions/resourceGroups/read",
"Microsoft.Resources/subscriptions/read",
"Microsoft.Network/loadBalancers/loadBalancingRules/health/action",
"Microsoft.Network/loadBalancers/health/action",
"Microsoft.Network/loadBalancers/backendAddressPools/health/action",
"Microsoft.Network/applicationGateways/getBackendHealthOnDemand/action",
"Microsoft.Network/applicationGateways/backendhealth/action",
"Microsoft.Compute/virtualMachineScaleSets/read",
"Microsoft.Compute/virtualMachineScaleSets/virtualMachines/read",
"Microsoft.Compute/virtualMachineScaleSets/networkInterfaces/read",
"Microsoft.Network/expressRouteCircuits/peerings/arpTables/read",
"Microsoft.Network/expressRouteCircuits/peerings/routeTables/read",
"Microsoft.Network/expressRouteCircuits/read",
"Microsoft.Compute/virtualMachineScaleSets/virtualMachines/instanceView/read"
],
"notActions": [],
"dataActions": [],
"notDataActions": []
}
]
}
}
What Counts Against IP Fabric License
See Licensing – Azure.