IP Fabric v7.2
Upgrade Version Policy
We support the following upgrade paths:
- The latest version in the previous major line → any version in the
current major line (for example,
6.10.7→7.2.19). - Any version in the current major line → any newer version in the current
major line (for example,
7.0.15→7.2.19).
Clearing Browser Cache
After upgrading IP Fabric to a newer version, you should see the Your
application has been updated and must be refreshed dialog in the main GUI.
It is usually sufficient to just click the Refresh button.
However, in case of issues with the main GUI or if you did not see the mentioned dialog, please force refresh your browser cache.
The key combination for doing this depends on your operating system. In your browser window with your IP Fabric appliance’s URL open, use one of the following key combinations:
- Windows:
Ctrl+F5 - macOS:
Command+Shift+R - Linux:
Ctrl+F5
This will only affect the browser cache for the IP Fabric appliance.
v7.2.19 (June 30th, 2025; GA)
SHA256 (ipfabric-update-7-2-19+0.tar.zst.sig) = eb6b972a4a8627a33f8e04de802da6f5894b399cd067718233d66e58bdd3c9d8
MD5 (ipfabric-update-7-2-19+0.tar.zst.sig) = bc1e3fe770a97eeed3520bb932154c02
SHA256 (ipfabric-7-2-19+0.qcow2) = cf1352dda443b290217d11127a0fa10bdec3d15e523f42797aad4d7e33957902
MD5 (ipfabric-7-2-19+0.qcow2) = 628751eb732abd3d76d3d581db1285d4
SHA256 (ipfabric-7-2-19+0.vmdk) = a3bb310c4e4d9ab9722c0482360ea3c106672744699f06241e9f1eedbd0532a3
MD5 (ipfabric-7-2-19+0.vmdk) = e652d43c0c5f1d681cb45383e072d8f4
SHA256 (ipfabric-7-2-19+0.vhdx.zst) = ffaa4c54bd8d510be7f42e753395daf02451ca56b110ebc24060ece43ef68844
MD5 (ipfabric-7-2-19+0.vhdx.zst) = 8d0d2946ba3f4d33d19a1fcf3313dfb9
SHA256 (unsupported-ESXi6.7U2-ipfabric-7-2-19+0.ova) = 14d8428c548291910811a55e3bd5eefacc817c0b68808a0c45a9c332511225cd
MD5 (unsupported-ESXi6.7U2-ipfabric-7-2-19+0.ova) = 7adecee1148b511df0e750ab380cf2e6
SHA256 (unsupported-ESXi7.0-ipfabric-7-2-19+0.ova) = 26401531cb865a550ea09cbf005dfb08d14a0031d1159e028c22858699ccafb1
MD5 (unsupported-ESXi7.0-ipfabric-7-2-19+0.ova) = 9bc66408c72d99323e702d359e711b6f
SHA256 (ESXi8.0-ipfabric-7-2-19+0.ova) = eb843527ae51613f6f6598f08ec35d3bc577fd1c0fe2637a32b886d69392be59
MD5 (ESXi8.0-ipfabric-7-2-19+0.ova) = 542f40aefa12347f8e5dd9d657199c1e
Fixes
BGP Communities Filtering
Starting with release 7.2.19, the new BGP communities filtering feature is fully supported on both manual and automated snapshots. Cisco IOS-XR compatibility has also been added.
Configuration Management Process Fails to Close SSH Sessions
Since 7.2.19, the Configuration Management process for HPE arubasw devices now properly terminates SSH connections and correctly detects login banners.
Known Issues
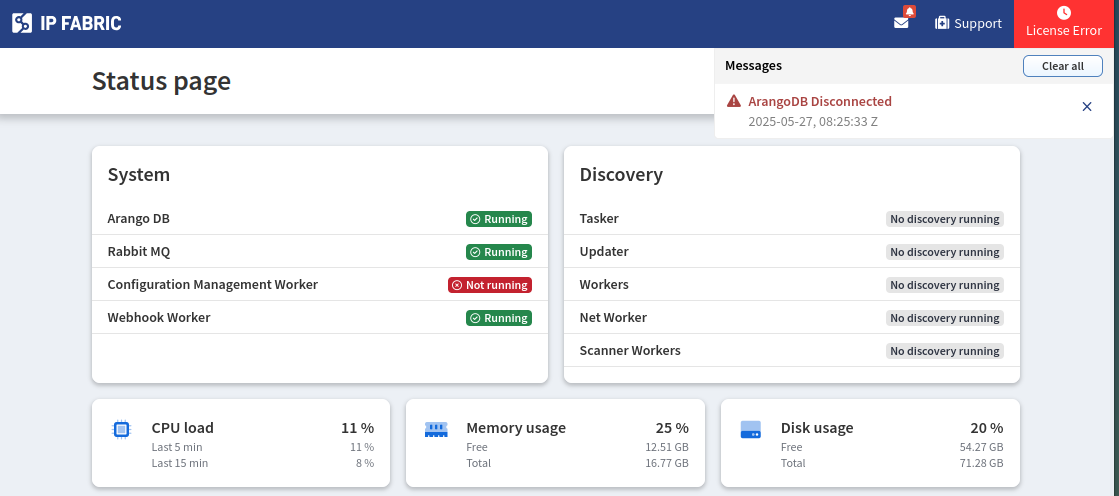
License or Database Errors After Upgrade
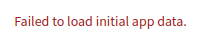
If the IP Fabric GUI redirects to the status page after an upgrade and displays errors such as License Error, ArangoDB Disconnected, or Failed to load initial app data, this may indicate an issue with the ArangoDB configuration.
To diagnose the issue:
-
Log in to the IP Fabric appliance via CLI and switch to the root user using
sudo -i. -
Check if ArangoDB is listening on port
8529via IPv6 (expected for IP Fabric7.2):root@IPF:~# lsof -i | grep 8529 | grep LISTEN arangod 952 arangodb 26u IPv6 19501 0t0 TCP *:8529 (LISTEN)If ArangoDB is bound to IPv4 instead, this likely causes the error:
root@IPF:~# lsof -i | grep 8529 | grep LISTEN arangod 874 arangodb 26u IPv4 20599 0t0 TCP *:8529 (LISTEN) -
Verify the
arangod.conffile in/etc/arangodb3is a symbolic link toarangod.conf.ipf. The directory should show:root@IPF:~# cd /etc/arangodb3 root@IPF:/etc/arangodb3# ls -lsa | grep arangod.conf 0 lrwxrwxrwx 1 root root 16 Nov 27 2023 arangod.conf -> arangod.conf.ipf 4 -rw-r--r-- 1 root root 1687 Feb 11 12:07 arangod.conf.ipf 4 -rw-r--r-- 1 root root 1696 Nov 27 2023 arangod.conf.ipf-orig
If the symlink is missing (i.e., arangod.conf is a regular file):
-
Run these commands to restore the symlink:
cd /etc/arangodb3/ mv arangod.conf arangod.conf.bkp ln -s arangod.conf.ipf arangod.conf systemctl restart arangodb3 -
Confirm the symlink exists and ArangoDB uses IPv6:
root@IPF:/etc/arangodb3# ls -lsa | grep arangod.conf 0 lrwxrwxrwx 1 root root 16 May 27 09:30 arangod.conf -> arangod.conf.ipf 4 -rw-r--r-- 1 root root 1697 May 27 09:22 arangod.conf.bkp 4 -rw-r--r-- 1 root root 1693 Jan 22 2021 arangod.conf.dpkg-old 4 -rw-r--r-- 1 root root 1687 Apr 23 13:42 arangod.conf.ipf 4 -rw-r--r-- 1 root root 1696 Mar 4 10:44 arangod.conf.ipf-orig root@IPF:~# lsof -i | grep 8529 | grep LISTEN arangod 876 arangodb 26u IPv6 17979 0t0 TCP *:8529 (LISTEN)
After these steps, the GUI should function correctly.
v7.2.17 (June 9th, 2025; GA)
Fixes
Something went wrong Error
After an upgrade a Something went wrong error when accessing the IP Fabric GUI after upgrading was shown. This issue was resolved in the 7.2.17 release but may still occur in rare situations. Clear the browser cache to resolve this issue.
v7.2.13 (May 21st, 2025; GA)
v7.2.5 (March 17th, 2025; EA)
API Endpoints Deprecation
The below API endpoints have been marked as deprecated and the intention is to remove them in version 7.5.
/tables/networks/gatewayRedundancy/tables/networks/networks
System Administration UI Removal
The System Administration UI on port 8443 has been deprecated in version 7.0 and is no longer accessible. All its functionalities have been replaced by an alternative:
RBAC Fixes
After reviewing our built-in RBAC policies, we have made the following changes. This is to ensure that the policies are more consistent with the intended use cases. If your roles require access to these endpoints, please create a custom RBAC policy and assign it to the required role(s).
These policies have been removed from the built-in others (ID of read) and moved to settings:
POST /os/generate-nimpee-cert: Generate IP Fabric certificatePOST /os/upload-nimpee-cert: Upload certificate to platformPOST /os/maintenance: Trigger platform maintenancePOST /os/snapshots-retention: Trigger snapshot retentionPOST /os/techsupport: Generate techsupport filePOST /os/clean-db: Clean system databasePOST /jobs/{key}/cancel: Cancel specific jobPOST /jobs/{key}/force-stop: Force stop running system jobPOST /jobs/{key}/stop: Stop running system jobGET /jobs/{key}/download: Return result of system job- With the introduction of the new Configuration Import/Export users without
settingspolicies are able to download and view all settings. - Our team is working on a feature to provide RBAC based on the type of file (configuration, snapshot, techsupport). This will be available in a future release.
- With the introduction of the new Configuration Import/Export users without
System upgrade improvements
- The upgrade UI has switched from basic HTTP authentication to cookie/session-based authentication.
- Downloading a remote upgrade package via the UI now displays download progress, which is also logged in the systemd journal.
- Improved timeout management provides better handling on systems with slow disk I/O or during network interruptions.
Layout Optimization for Large Circular Graphs
Circular graphs with over 100 nodes experienced slow rendering and oversized layouts due to complex line-crossing minimization calculations. This also impacted snapshot discovery/loading performance due to prolonged node position caching.
For graphs exceeding 100 nodes, we now automatically apply the universal layout instead of the circular layout. This ensures:
- Faster rendering (reduced layout computation time)
- Improved readability of large graphs
- Optimized snapshot performance (quicker node position caching)
The layout type change (circular → universal) is not yet reflected in API responses or the UI. This visibility will be added in an upcoming release.
New Features
Configuration Import/Export
- We have developed a new feature that allows you to import and export configurations of the IP Fabric application across multiple IP Fabric instances. More details can be found on the Configuration Import/Export page.
Automated SSO
- We have developed a new script to simplify the SSO setup process for the IP Fabric application. More details can be found on the Automated Single Sign-On (SSO) page.
Azure Network Load Balancers (NLB) support
-
Data collection and end-to-end path lookup via NLB nodes are supported. However, path lookup via Azure private links is not supported yet.
Do not forget to update IAM policy
To collect Azure Network Load Balancers, the corresponding IAM policy must be updated. You can download the new policy here.
Enhanced BGP Community Controls for Optimized Discovery
- Introduced per-device, per-protocol (IPv4/IPv6), and per-VRF BGP community configurations to limit downloaded routes during discovery.
- This feature prioritizes community-based filtering over global thresholds, ensuring precise data collection while reducing processing time. Ideal for large-scale networks with extensive BGP tables. For more information see Routing
Connections between IPsec & VXLAN tunnel endpoints now visible in path-lookup
- For easier identification of where IPsec and VXLAN tunnels start and end, especially when traversing multiple devices, direct links between tunnel endpoints are now visible in path lookups. More details can be found in IPsec & VXLAN tunnel endpoints.
BGP Route Collection Enhancement
We have introduced filtered BGP route collection support, allowing network administrators to explicitly define which networks to collect. This enables focused BGP route analysis while optimizing system resources across Cisco IOS/IOS-XE, IOS-XR, NX-OS, Juniper JunOS and Arista EOS platforms.
For detailed information about the new API endpoints and configuration options, see BGP Route Collection API.
Improvements
GUI
- We have updated default tabs settings for consoleServer devices in Device Explorer: added Serial Ports, removed QoS, MAC and Port Channel. This resets previous tab settings for this device type.
- Edges in topology graphs now support multiple labels, which can be displayed either inline or on separate lines. These settings are customizable in the Visualization Setup panel of the Network Viewer, allowing configuration for each protocol or group type individually.
- Additional columns were added to Inventory → Interfaces table, all hidden by default:
Clearing TypeClearing ValueLast Input TypeLast Input ValueLast Output TypeLast Output Value
- An additional column was added to the Inventory → Devices table and is hidden by default:
Credentials Notes
- Global filter now allows for selecting all possible values of given attribute using the
Select alloption.
Advanced Filters
-
Device Attribute-Based Advanced Filters now supports Attributes as a device property.
This allows you to:
- Filter data using predefined Attributes, such as
siteName. - Use custom Attributes for more specific filtering.
- Filter data using predefined Attributes, such as
- For a complete list of properties and supported tables, refer to Technology Tables – Device-Based Advanced Filters.
Discovery Settings
- Saving discovery settings with missing or expired credentials is now allowed. Users can decide whether the missing data is important for running the discovery or can add the data later. Clear messages and dialogs will inform users of any potential issues.
Network Discovery
-
New Capabilities – Cisco (FTD), Fortinet (FortiGate), PaloAlto (PAN-OS)
- Support for URL filtering has been added.
- In Path Lookup under
Advanced Packet Options, new search fields are now available:Site category: Matches the name of a URL filter category. Works for both built-in and custom categories. The field accepts regex if multiple categories are needed in the result.URL / DOMAIN: Matches a specific URL against applicable security rules.
- New Capabilities – PaloAlto (PAN-OS)
- Support for URL-type objects of
External Dynamic Listhas been added.
- Support for URL-type objects of
- New Capabilities – Fortinet (FortiGate)
- Support for URL-type objects of
External Resourcehas been added.
- Support for URL-type objects of
Vendor Support and Improvements
- Added Silver Peak API key authentication support.
- Added IPv6 BGP neighbors support for Arista (EOS), Cisco (IOS, IOS-XE, NX-OS), FS (FSOS), PaloAlto (PAN-OS).
- Added support for IPv6 BGP Route limit - see documentation
- Arista: EOS
- Cisco: NX-OS, IOS, IOS-XE, IOS-XR, Viptela
- Juniper: JunOS
- Nokia: TiMOS
- Added URL filtering support in firewall rules for Cisco (FTD), Fortinet (FortiGate), PaloAlto (PAN-OS).
- Added support for SR-MPLS TE with BGP On-Demand Next Hop (ODN) functionality for Cisco (IOS-XR).
- Added threat feeds support for FortiGate firewalls (IP lists only).
- The HP vendor has been renamed to HPE.
- The bookmark
Detailfor all AWS devices has changed. The differences are:- The
Familycolumn value is now empty (previously was set toec2) - The
Versioncolumn value is now empty (previously was set to2016-11-15)
- The
- Added support for Nokia TiMOS version 23 and above
Technology Tables
-
Unmanaged Neighbors Detail – Fixed an issue in the Technology → Interfaces → Connectivity matrix → Unmanaged Neighbors Detail table where Intent Verification rules could incorrectly highlight rows for specific datasets. Unique row IDs have been enforced to resolve the inconsistency.
Important
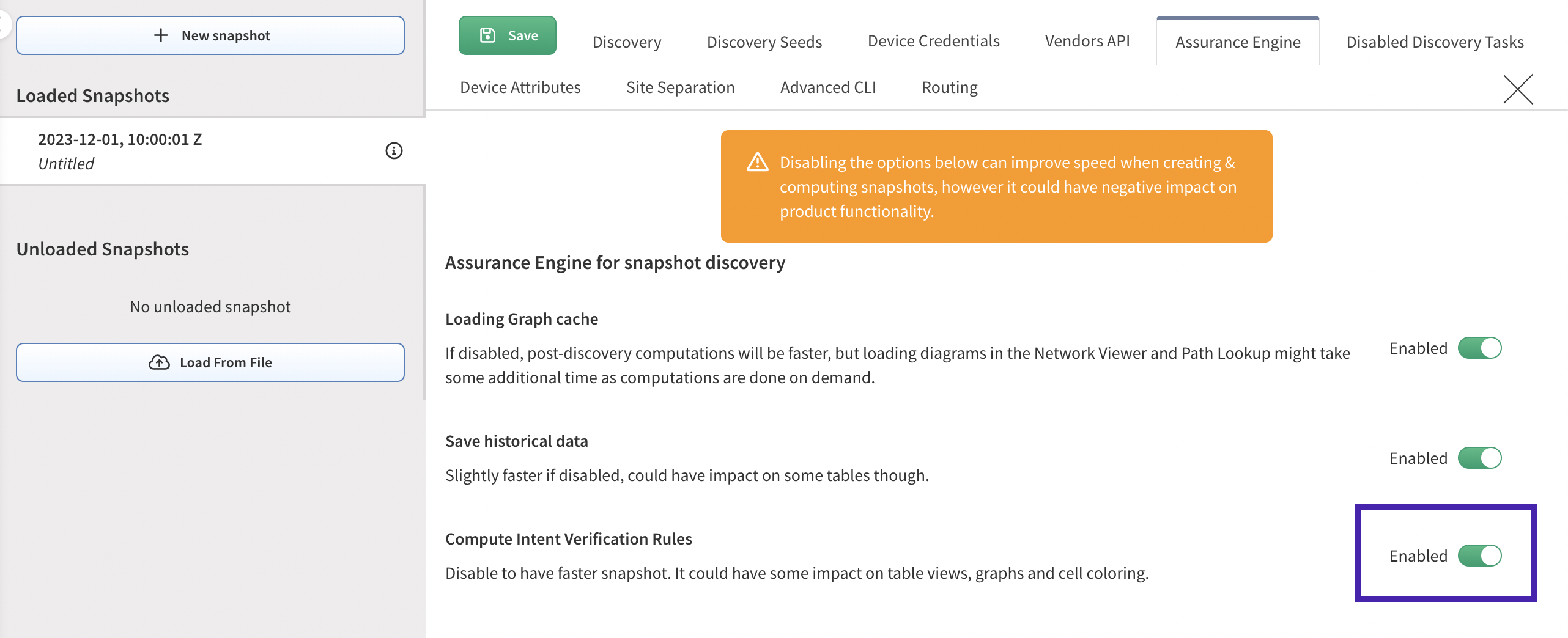
If Intent Verification rules were configured for this table, you may need to trigger their recalculation. To do this, you can either:
- In local settings of the relevant snapshot(s), toggle “Compute Intent Verification” off, save settings, then toggle the rule back on; or
- Manually unload and reload the relevant snapshot(s)
Site separation
- Devices now automatically inherit their site name from connected peers via CDP/LLDP, STP topology neighbors, or devices in the same L3 network, in order of priority, when rule Try to assign devices without sites based on device neighborship is enabled.
Experimental Features
Newly added features which need to be explicitly enabled in service files. You can enable these yourself using our feature documentation or if you are not comfortable self-enabling these features or need further clarification, contact our Support or Solution Architect team. We will gladly help you.
Configuration Management Optimizations
To accelerate device configuration retrieval, you can try to enable different Git performance optimizations for configuration management.